In this post, we are going to talk about the importance of time factor in attribution of malicious domain. The "malicious domain attribution": it means the different set of characteristics that are mapped or analyzed to gain control of the malicious domain. It is very critical from analysis perspective. Yesterday, we had a very interesting case about the malicious domain attribution. There are certain facts that are required to be understood for executing reverse attacks on the malicious domains. We have found that timing plays a crucial role in successfully attributing the malicious domains. What happened exactly ?
Step 1: We received a FedEx Phishing email embedded with some malicious links.
Step 2: The source of the phished email was analyzed and related information was collected.
Step 3: The links were traced to understand the source of the problem.
Step 4: The browser was redirected to malicious domain (First Hop) having obfuscated code in it.
Step 5: The obfuscated code was deobfuscated and we were served with a dynamic iframe code.
Step 6: On tracing the source in malicious iframe, the browser fetched an obfuscated code from
the BlackHole - Browser Exploit Pack (BEP) hosted on other domain (Second Hop).
Step 7: The code served by BlackHole BEP was again obfuscated, which on deobfuscation provided
a plugin detection JavaScript that fingerprinted the versions of various installed plugins.
Step 8: A malicious JAR was framed inline during fingerprinting of the browser plugins.
Step 9: On successful exploitation of a Java vulnerability, an executable file was served.
Actors - BlackHole, Cridex Trojan.
Compromised Domains - Word Press website.
The communication flow is presented below:
Interesting Technique:
HTTP Parameter Iteration
It is a simple technique in which HTTP parameters are iterated with different numbers to see if we get a different output or not. For example:- this technique is fruitful when the analyst wants to verify that a malicious link allows different files to be downloaded from the same URL. Sometimes this technique is worth giving a shot. We followed the same process and got same executables with different names as shown below:
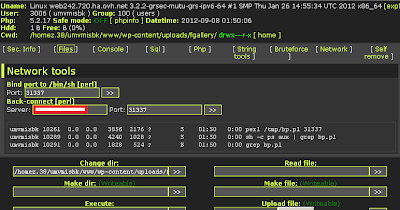
We have the executable files, the JAR files and other information. At this point, the complete infection scenario is presented. What else? Do we have to stop here after the analysis? We don't believe so. What should be the target now? Exactly- finding vulnerabilities in the server hosting malicious websites. Fortunately, we found a vulnerability in the server that allow us to access a PHP shell on the server as follows:
We started looking for configuration files as shown below:
After all this point, we had an access to server (First Hop) hosting the initial infection page. But, this process did not came out to be that fruitful as we were expected. We were in hurry to find the access information or other critical data that provided us with complete control. Unfortunately, this time the attacker was still active on the malicious domain.
As a result, within no time, we were getting forbidden messages ( no further access to the server). Ofcourse, the attacker came to know that the server has been compromised. The attacker removed the content from the server. The result is shown below:
That's the complete information of the case that we encountered recently. Now the questions, thinking points and lessons to be learned are as follows:
1.
Time window plays a critical role in these types of cases.
Do we have to act stealthy? Should we wait for sometime if we get an access to the malicious
server?
2.
The time gap (window) or reaction time definitely impacts the analysis.
Is this right to explore the malicious server right away without waiting?
At this point, we believe that it is a problem of choice, a kind of double edged sword.But for sure, we made a choice not to wait further and act in a dormant manner. Our decision was not that fruitful but it helped us to learn the importance of time window in performing attribution of malicious domains.
If you have other views, please share :) We will be more than happy to discuss our experiences.