An Official Malware Research Blog of SecNiche Security Labs. Analysis, straight from the hidden and underground.
Sunday, December 2, 2012
HITB EZine : Bot Wars - The Game of Win32/64 TakeOver
Botnets have been in existence for years. Third Generation Botnets (TGB’s) use sophisticated attack vectors to infect users at a large scale. Botnets are cyber weapons that can jeopardize the integrity and security of the critical infrastructure on the Internet. There is an insidious war going among different generations’ of botnets to exploit the target systems. This concept is termed as bot wars. This article explores the details of bot wars and how the bots kill each other to control the infected systems.
The paper is out in the 9th edition of HITB Ezine. Fetch the magazine from here: http://magazine.hackinthebox.org/issues/HITB-Ezine-Issue-009.pdf
Wednesday, October 10, 2012
Attribution - Team Cyberthack and The Game of Facebook Phishing Attack - Tracking Back
This Facebook case study is an interesting one and based on the ongoing Facebook phishing attack leading to malware. Interestingly, the attack seems to be launched by the Indonesian and Spanish hackers considering the languages used in the deployed code. Our team came across a Facebook phishing email embedded with a video and other malicious links. Every single URL pointed to a same domain. The Facebook message embedded in the email carried a notification message that says something as follows:
""Miiiii lindoooo! Ahahahaha this videoo muestrezzz not what to nadiesss = $ $ $ $ ZIII? Tiii is for! Because? Yoooo muxiiiisisisisizimoooo amoooo you! Muxo like me will I require your videooo montonezzzz!! porfiz when estez at ............ "Read more This video was ranked No one under 18."
The original message is presented below:
"Miiiii lindoooo!!! ahahahaha este videoo no se lo muestrezzz a nadiesss =$$$$ ziii ?? es solo para tiii!! porque ? yoooo te amoooo muxiiiisisisisizimoooo!!! me gusto muxo tu videooo te requiero montonezzzz!!!! porfiz cuando estez en. ..... . ....." Leer mas
Este video fue clasificado Prohibido para menores de 18 años .
The phishing email was structured like as shown below:
Before looking into the kind of malware served by this phishing attack, let's dissect the other relevant information gathered from this malicious domain. The facts are discussed as follows:
1. The domain was compromised by the Cyberthack Team.
2. On analyzing further, we got an information that was embedded somewhere in the web pages about the profile of a user. We cannot say this profile is legitimate or fake at this point of time but, it is worthwhile to look into this. The profile is presented below:
3. Some of the JavaScripts that are used in this malware domain are taken from the - http://cirebon-cyber4rt.blogspot.com/. Guys, tt is always good to remove the comments when you are doing this kind of job.
4. Again, a configuration flaw in the web server running on this malicious domain allowed us to access the
a custom statistics page that pointed out the visitors visiting that link. It is shown below:
The language used in this page is Spanish. It is easy to decipher the number of visitors that visited this page
5. The malicious link downloaded facebook.exe executable on the victim machine. Some of the facts
are listed below:
5.1 The malicious program is written in Visual Basic.
5.2 No packer is used to pack the critical sections. No code obfuscation is used.
5.3 The malicious program used a reference to TortoiseBlame -http://tortoisesvn.tigris.org/blame.html.
It seems like the malware tries to look legitimate.
5.4 The malware executes silently in the system and on successful installation, opens facebook.com web
page.
5.5 The malware creates wincal.exe in the %systemroot% folder and uses registry to load it. It is again a
Visual Basic file.
For additional check, the virus total analysis is here: https://www.virustotal.com/file/a64c6d344626ca983979042485a2b8b271ae08f1e411511227700591c2418ac1/analysis/
Stay secure.
Note: This attack is still active.
Thursday, September 20, 2012
Did You Order HDTV from Amazon? - Yes | No, Phishers Targeting Amazon Brand !
The concept is the same so as the attack. This time attackers are using Amazon brand to spread infections on the Internet. The phishing email is drafted really well and shows that an order of ne product (HDTV) has been processed. The email looks like as follows:
The browser is redirected to the web page showing the notification as follows:
The script looks like as shown below:
The deobfuscation results in the following code.
Again, the iframe loads content from third-party domain hosting Browser Exploit Pack (BEP). The interesting fact is that, we received a number of emails within a span of time. Every new phishing email has a new embedded URL as follows:
hxxp://shuraki.com/wp-admin/hdtvamazon.html [WordPress]
hxxp://swishmedia.ca/clients/amazinhdtv.html [Generic]
hxxp://tainguyenso.com/admincp/amazinhdtv.html [V Bulletin]
These emails look very genuine and authentic. It is highly advised that to be paranoid and think twice before interacting with these emails.
Check previous post about LinkedIn Phishing Attack - http://secniche.blogspot.com/2012/08/linekedin-invitation-phishing-blackhole.htmlhttp://secniche.blogspot.com/2012/08/linekedin-invitation-phishing-blackhole.html
Elsevier's Computer Network Journal - Understanding the Design of SpyEye Botnet
We have contributed a paper on complete details of SpyEye design in Elsevier's Computer Network journal.
Abstract: "Botnet malware is improving with the latest (3rd) generation exemplified by the SpyEye and Zeus botnets. These botnets are important to understand because they target online financial transactions, primarily with banks. In this paper, we analyze the components from multiple generations of the SpyEye botnet in order to understand both how it works and how it is evolving. SpyEye is a sophisticated piece of malware with a modular design that eases the incorporation of improvements. We will discuss in detail the complete framework of SpyEye botnet consisting of the Bot Development Kit (BDK), the plugin architecture, the backend storage server, the bot design and the web-based Command and Control (C&C) management system. In addition, we also examine the techniques used by SpyEye to steal money."
The paper is still in press but can be found at: http://www.sciencedirect.com/science/article/pii/S1389128612002666.
Enjoy!
Abstract: "Botnet malware is improving with the latest (3rd) generation exemplified by the SpyEye and Zeus botnets. These botnets are important to understand because they target online financial transactions, primarily with banks. In this paper, we analyze the components from multiple generations of the SpyEye botnet in order to understand both how it works and how it is evolving. SpyEye is a sophisticated piece of malware with a modular design that eases the incorporation of improvements. We will discuss in detail the complete framework of SpyEye botnet consisting of the Bot Development Kit (BDK), the plugin architecture, the backend storage server, the bot design and the web-based Command and Control (C&C) management system. In addition, we also examine the techniques used by SpyEye to steal money."
The paper is still in press but can be found at: http://www.sciencedirect.com/science/article/pii/S1389128612002666.
Enjoy!
Monday, September 17, 2012
Insidious Banking Malware and Proxy-auto Config (PAC) - A Step towards Mal-Proxying
What is PAC?
PAC is a technique to implement proxy configurations based on the rules provided in the configuration file. The browser chooses the appropriate proxy server for the configured URLs. PAC is implemented in a sandbox and few JavaScript functions are allowed to be used in the PAC files. For more details about PAC, the excellent resource is here - http://findproxyforurl.com/why-pacwpad/ . PAC uses FindProxyForURL() function to implement this functionality. Have a look at one of the example listed here: http://findproxyforurl.com/example-pac-file/.
Why malware uses PAC?
The concept is straightforward. On the infected machine, the malware downloads the obfuscated PAC file from the server. This allows the malware authors to force the rules defined in the PAC file on the active browsers. It means the malware can push the browser to choose a proxy server based on the URL rules configured in the PAC file. In simpler terms, if a user tries to open a banking website, the browser connects to the proxy server and the traffic is routed through it.
Let's look into the PAC file used by the banking malware:
The file contained an array of elements in the hexadecimal format. The next step is to see what is hidden behind this. Removing "\x" and applying hexadecimal to ASCII converter, we get the elements as shown below:
So as expected, we get the domains configured in the PAC file. Whenever, a user opens the domain listed above, the browser connects to the given proxy server and routes the web traffic through it. Interesting !. Let's look at the implementation of FindProxyForURL() function.
The above-referenced code uses shExpMatch - which attempts to match hostname or URL to a specified shell expression, and returns true if matched. More details can be found here: http://findproxyforurl.com/pac-functions/.
var _0x355ax4=_0x4919[0] : refers to the first element in the array which is the "PROXY 46.23.77.172".
if(shExpMatch(_0x355ax3,_0x355ax6)){return _0x355ax4;}; - you know what it means :) . If the domain is matched then force the browser to connect to the given proxy server. The same process goes for the rest of the provided rules.
This shows that how exactly the malware uses the PAC concept for malicious operations.
Enjoy!.
Saturday, September 8, 2012
Malicious Domain Attribution - The Criticality of Timing
Step 1: We received a FedEx Phishing email embedded with some malicious links.
Step 2: The source of the phished email was analyzed and related information was collected.
Step 3: The links were traced to understand the source of the problem.
Step 4: The browser was redirected to malicious domain (First Hop) having obfuscated code in it.
Step 5: The obfuscated code was deobfuscated and we were served with a dynamic iframe code.
Step 6: On tracing the source in malicious iframe, the browser fetched an obfuscated code from
the BlackHole - Browser Exploit Pack (BEP) hosted on other domain (Second Hop).
Step 7: The code served by BlackHole BEP was again obfuscated, which on deobfuscation provided
a plugin detection JavaScript that fingerprinted the versions of various installed plugins.
Step 8: A malicious JAR was framed inline during fingerprinting of the browser plugins.
Step 9: On successful exploitation of a Java vulnerability, an executable file was served.
Actors - BlackHole, Cridex Trojan.
Compromised Domains - Word Press website.
The communication flow is presented below:
Interesting Technique: HTTP Parameter Iteration
It is a simple technique in which HTTP parameters are iterated with different numbers to see if we get a different output or not. For example:- this technique is fruitful when the analyst wants to verify that a malicious link allows different files to be downloaded from the same URL. Sometimes this technique is worth giving a shot. We followed the same process and got same executables with different names as shown below:
We started looking for configuration files as shown below:
After all this point, we had an access to server (First Hop) hosting the initial infection page. But, this process did not came out to be that fruitful as we were expected. We were in hurry to find the access information or other critical data that provided us with complete control. Unfortunately, this time the attacker was still active on the malicious domain. As a result, within no time, we were getting forbidden messages ( no further access to the server). Ofcourse, the attacker came to know that the server has been compromised. The attacker removed the content from the server. The result is shown below:
1. Time window plays a critical role in these types of cases.
Do we have to act stealthy? Should we wait for sometime if we get an access to the malicious
server?
2. The time gap (window) or reaction time definitely impacts the analysis.
Is this right to explore the malicious server right away without waiting?
At this point, we believe that it is a problem of choice, a kind of double edged sword.But for sure, we made a choice not to wait further and act in a dormant manner. Our decision was not that fruitful but it helped us to learn the importance of time window in performing attribution of malicious domains.
If you have other views, please share :) We will be more than happy to discuss our experiences.
Tuesday, August 28, 2012
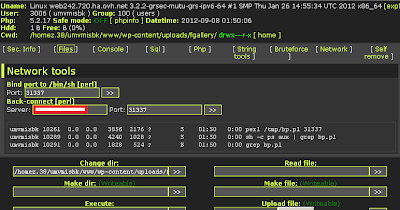
Intuit Phishing Campaign - Mighty BlackHole in Action
Intuit phishing campaign has been started today. The structure and concept of the attack is the same as discussed earlier. Let's dissect the details of this campaign. The email comes to your inbox in the format as presented below:
The accompanied link is : hxxp://numerodedicato.altervista.org/blog/wp-content/uploads/fgallery/updint.html. On visiting the link, the user finds a webpage with a following layout:
The message looks interesting. The webpage is executing another JavaScript to load content from another third-party domain. The details of this deobfuscated script are present here: http://pastebin.com/MVCH8M3N
The obfuscation provided us with an iframe that is downloading content from the following URL: hxxp://roadmateremove.org/main.php?page=9bb4aab85fa703f5
The obfuscated plugin script is here : http://pastebin.com/biZnVwMD
The deobfuscated plugin script is here : http://pastebin.com/hsKKn6EP
Many of the AV engines shows this website as benign. But, this domain hosting a BH exploit Pack. Let's see further:
On deobfuscation we get an applet code as follows:
Something seems suspicious, with Pre.jar file here. Further, the request to this link : hxxp://roadmateremove.org/data/hhcp.php?c=8896e loads the iframe for the plugin detection code. On successful verification and fingerprinting the Pre.jar file is served on the vulnerable systems. A quick check on virus-total only provides a reference to Blackhole exploit.
Check: https://www.virustotal.com/file/65ac3d0ef75cad088c80bcb238fe6206c42866a8e73676f5b5dd6b235871f874/analysis/1346173365/
Definitely a Java exploit in action.
This analysis is based on a specific link accompanied with this sample. The embedded links might change with other phishing emails.
Be Secure.
The accompanied link is : hxxp://numerodedicato.altervista.org/blog/wp-content/uploads/fgallery/updint.html. On visiting the link, the user finds a webpage with a following layout:
The message looks interesting. The webpage is executing another JavaScript to load content from another third-party domain. The details of this deobfuscated script are present here: http://pastebin.com/MVCH8M3N
The obfuscation provided us with an iframe that is downloading content from the following URL: hxxp://roadmateremove.org/main.php?page=9bb4aab85fa703f5
The obfuscated plugin script is here : http://pastebin.com/biZnVwMD
The deobfuscated plugin script is here : http://pastebin.com/hsKKn6EP
Many of the AV engines shows this website as benign. But, this domain hosting a BH exploit Pack. Let's see further:
On deobfuscation we get an applet code as follows:
Something seems suspicious, with Pre.jar file here. Further, the request to this link : hxxp://roadmateremove.org/data/hhcp.php?c=8896e loads the iframe for the plugin detection code. On successful verification and fingerprinting the Pre.jar file is served on the vulnerable systems. A quick check on virus-total only provides a reference to Blackhole exploit.
Check: https://www.virustotal.com/file/65ac3d0ef75cad088c80bcb238fe6206c42866a8e73676f5b5dd6b235871f874/analysis/1346173365/
Definitely a Java exploit in action.
This analysis is based on a specific link accompanied with this sample. The embedded links might change with other phishing emails.
Be Secure.
Tuesday, August 7, 2012
LinkedIn Invitation Phishing - BlackHole in Action (2)
Last time we discussed about the LinkedIn phishing attack, here - http://secniche.blogspot.com/2012/06/linkedin-phishing-attack-exploit.html. Within last 2-3 days, there has been significant increase in LinkedIn invitation emails which are malicious in nature. The attackers are exploiting the brand names as discussed earlier in our post on At&T Phishing attack here: http://secniche.blogspot.com/2012/08/at-phishing-attack-blackhole-back-in.html.
The Linkedin phishing attack is again based on the same pattern and some of the details are discussed in this post. The phishing email layout is presented below:
The Linkedin phishing attack is again based on the same pattern and some of the details are discussed in this post. The phishing email layout is presented below:
Visiting the link resulted in following message.
The execution process is the same as discussed earlier in the phishing attacks. The deobfuscated script is shown below:
The HTML content of the phishing email is here: http://pastebin.com/tbyxaEXs.
The complete script is here: http://pastebin.com/kvnvMrma
The script patterns are the same except the the URL of the malicious domain varies. Just be proactive and be paranoid in interacting with these types of emails.
Monday, August 6, 2012
AT&T Phishing Attack - BlackHole Back in Action
Attackers are using legitimate organizations' brand names to distribute phishing emails to a large sections of users. This time AT&T brand name is used to deliver phishing emails. We have been receiving these emails continuously. These first attempt made by the phisher was failed because the injected links were not embedded in a right manner which results in useless phishing attempt. The very next day, we received the similar email but this time phishers were right at the target. The second time email contained malicious links. Let's have a look at the phishing email message:
On surfing the embedded links, the browsers was forced to visit the malicious domain as presented below:
This page contains obfuscated malicious iframe that renders dynamically to load a plugin detection script from third-party domain that fingerprinted the users' environment and served the required exploit. Blackhole BEP exploit has been used to distribute exploits against vulnerable browsers and plugins. The iframe loads the webpage which contains plugin detection script. The page shows a redirection message as follows:
The HTML content of the phishing email is pasted here - http://pastebin.com/epGAx7fr
The malicious script (deobfuscated) can be found here : http://pastebin.com/Ne4j5zmd
This link - hxxp://voicecontroldevotes.info/main.php?page=6df8994172330e77 loads the plugin fingerprinting script and connects back with BlackHole BEP.
This host (IP) has been used to register different domain names that have been used for spreading malware using BlackHole. Query here - http://www.malwaredomainlist.com/mdl.php?search=78.87.123.114&colsearch=All&quantity=50
These emails are delivered as legitimate and spam detection engine fails to provide any protection. Try not to fall prey to these phishing attempts.
Virus Bulletin - ICE IX Bot Paper
This month, we have published a paper on ICE 1X analysis in virus bulletin magazine.
Abstract: The ICE IX bot is considered to be a descendent of the
Zeus botnet because it uses some of Zeus’s source code. ICE IX communicates using the HTTP protocol, so it can be considered to be a third generation botnet. While it has been used for a variety of purposes, a major threat of ICE IX comes from its manipulation of banking operations on infected machines. As with any bot, infection results in establishing a master-slave relationship between the
botmaster and the compromised machine"
Subscribe the magazine : http://www.virusbtn.com/virusbulletin/archive/2012/08/vb201208-ICE-bot
The paper will be released on the website after the contractual obligations are over.
Enjoy!
Abstract: The ICE IX bot is considered to be a descendent of the
Zeus botnet because it uses some of Zeus’s source code. ICE IX communicates using the HTTP protocol, so it can be considered to be a third generation botnet. While it has been used for a variety of purposes, a major threat of ICE IX comes from its manipulation of banking operations on infected machines. As with any bot, infection results in establishing a master-slave relationship between the
botmaster and the compromised machine"
Subscribe the magazine : http://www.virusbtn.com/virusbulletin/archive/2012/08/vb201208-ICE-bot
The paper will be released on the website after the contractual obligations are over.
Enjoy!
Thursday, August 2, 2012
Digital Forensics Magazine - Dismantling SMS based Two-factor Authentication - Malware
 We have recently published details of SMS based Two-factor authentication attack used by the Third Generation Botnets (TGBs) in which both system and mobile platforms are exploited. If you remember, Spitmo, Zitmo and other variants are used to accomplish this kind of attack.
We have recently published details of SMS based Two-factor authentication attack used by the Third Generation Botnets (TGBs) in which both system and mobile platforms are exploited. If you remember, Spitmo, Zitmo and other variants are used to accomplish this kind of attack.
Outline: "Malware is impacting the security and integrity of the World Wide Web especially for banks and financial institutions. This article looks at a new exploitation technique used by malware to circumvent two-factor authentication."
About DF: "Digital Forensics Magazine is a quarterly features and news magazine from the world of computer and cyber crime and digital forensics."
Right now, magazine is available for subscribers only,but you can also read it online by creating an account.
http://www.digitalforensicsmagazine.com/index.php?option=com_content&view=article&id=792&Itemid=1
Enjoy !
Sunday, July 29, 2012
Sunday, July 15, 2012
HOPE 2012 Presentation - Advancements in Botnet Attacks
Monday, July 2, 2012
IEEE Security and Privacy (PrePrint) - Targeted Cyber Attacks - A Superset of APTs
Our paper on "Targeted Cyber Attacks - A Superset of Advanced Persistent Threats" is available in preprint at:
http://www.computer.org/csdl/mags/sp/preprint/msp2012990114-abs.html
Abstract - Cybercrime increasingly impacts the online world, and targeted attacks are playing a significant role in disrupting the online social and economic model. In addition, nations are facing threats as a result of targeted attacks. In this paper we examine a variety of components and techniques that are brought together to bring about targeted attacks.
I will update the details once it is published as a part of hard copy.
http://www.computer.org/csdl/mags/sp/preprint/msp2012990114-abs.html
Abstract - Cybercrime increasingly impacts the online world, and targeted attacks are playing a significant role in disrupting the online social and economic model. In addition, nations are facing threats as a result of targeted attacks. In this paper we examine a variety of components and techniques that are brought together to bring about targeted attacks.
I will update the details once it is published as a part of hard copy.
Sunday, July 1, 2012
BlackHole + Java Array Exploit - Rising High
During our analysis, we have seen that several of the websites have been infected with obfuscated JavaScripts that point to one or the other Browser Exploit Pack (BEP). Typically, BlackHole is the primary weapon for automated infections using Drive-by-download attacks. Recently, another high traffic website is found to be running malicious script that is loading BlackHole to trigger infection.
Java array exploit is on rise nowadays. Microsoft has discussed about the details of this vulnerability at: http://blogs.technet.com/b/mmpc/archive/2012/03/20/an-interesting-case-of-jre-sandbox-breach-cve-2012-0507.aspx.
The obfuscated script is present here - http://pastebin.com/nVQcmMsM. The script deobfuscates to the following code as follows:
The URL's are designed to use no-ip or dynamic dns service. According to Wikipedia, "Dynamic DNS or DDNS is a method of updating, in real time, a Domain Name System (DNS) to point to a changing IP address on the Internet. This is used to provide a persistent domain name for a resource that may change location on the network."
We mapped the required IP and doing some behavioral analysis, a plugin detection script was found as present on the following lnk:
Obuscated Code - http://pastebin.com/rK0NaAMh.
Deobfuscated Plugin Detection code - http://pastebin.com/QxiXVRcG
The code fingerprints the browser for running different set of plugins. On finding the vulnerable version of Java plugin, the script downloads the malicious jar file running specific Java exploit.
The decompiled code is present here: http://pastebin.com/5FWMUEtP
Java exploits have become popular. We have also discussed earlier about top 5 Java exploits here: http://secniche.blogspot.com/2011/05/finest-5-java-exploit-on-fire.html.
Java array indexing vulnerability is the new kid in the town. Refer vulnerability - http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0507.
Java array exploit is on rise nowadays. Microsoft has discussed about the details of this vulnerability at: http://blogs.technet.com/b/mmpc/archive/2012/03/20/an-interesting-case-of-jre-sandbox-breach-cve-2012-0507.aspx.
The obfuscated script is present here - http://pastebin.com/nVQcmMsM. The script deobfuscates to the following code as follows:
The URL's are designed to use no-ip or dynamic dns service. According to Wikipedia, "Dynamic DNS or DDNS is a method of updating, in real time, a Domain Name System (DNS) to point to a changing IP address on the Internet. This is used to provide a persistent domain name for a resource that may change location on the network."
We mapped the required IP and doing some behavioral analysis, a plugin detection script was found as present on the following lnk:
Obuscated Code - http://pastebin.com/rK0NaAMh.
Deobfuscated Plugin Detection code - http://pastebin.com/QxiXVRcG
The code fingerprints the browser for running different set of plugins. On finding the vulnerable version of Java plugin, the script downloads the malicious jar file running specific Java exploit.
The decompiled code is present here: http://pastebin.com/5FWMUEtP
Java exploits have become popular. We have also discussed earlier about top 5 Java exploits here: http://secniche.blogspot.com/2011/05/finest-5-java-exploit-on-fire.html.
Java array indexing vulnerability is the new kid in the town. Refer vulnerability - http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0507.
Thursday, June 14, 2012
Digging Inside Tinba Malware - A Walkthrough
Other researchers have presented details about Tinba which can be found here - http://www.csis.dk/en/csis/news/3566/
We looked specifically at communication patterns of Tinba. As we know, bots are hooking browsers and performing Web Injects to gain control over the browser communication channel. Other interesting facts about Tinba is as follows:
- The accompanied binary is written in MASM/TASM and having size of 20 KB. Compiling with MASM reduces the size of the binary to great extent.
- The binary executes as : tinba.exe --- bin.exe --- readme.exe --- winver.exe The dropper actually installs the bin.exe file in the application directory and then deletes the wrapper (binary). File bin.exe resides in the directory permanently.
- Adds run entry here - HKCU\Software\Microsoft\Window\CurrentVersion\Run
- Tinba hooks browser processes and make them unstable, so there is a possibility that users might encounter several crashes in browsers while running or surfing internet. The browser works fine when the system is rebooted.
- As the tinba injects in explorer.exe, the binding occurs very fast when bot has to send SYN packet and to receive reply from the C&C server. The connection is continuous but TCPView is not fruitful in this case because the connection open and closes readily. TDIMon tools gives you the low level traffic details by inspecting the Transport Driver Interface as presented below:
explorer.exe:168 TDI_SEND TCP:0.0.0.0:2552 82.165.37.127:80 SUCCESS-2941 Length:353
explorer.exe:168 TDI_SEND TCP:0.0.0.0:2552 82.165.37.127:80 SUCCESS-2942 Length:9
explorer.exe:168 TDI_EVENT_CHAINED_RECEIVE TCP:0.0.0.0:2552 82.165.37.127:80 SUCCESS
explorer.exe:168 TDI_EVENT_DISCONNECT TCP:0.0.0.0:2552 82.165.37.127:80 SUCCESS RELEASE
explorer.exe:168 TDI_SEND TCP:0.0.0.0:2545 82.165.37.127:80 SUCCESS Length:353
explorer.exe:168 TDI_SEND TCP:0.0.0.0:2545 82.165.37.127:80 SUCCESS Length:9
explorer.exe:168 TDI_EVENT_RECEIVE TCP:0.0.0.0:2545 82.165.37.127:80 SUCCESS
explorer.exe:168 TDI_EVENT_DISCONNECT TCP:0.0.0.0:2545 82.165.37.127:80 SUCCESS RELEASE
One can notice that the events are happening very fast. The below presented figure shows the TCP/IP pattern in injected explorer.exe process.
 |
| Tinba Hooking Explorer - TCP/IP Pattern |
When forms are submitted over HTTP/HTTPS, the Firefox raises an alert box for notifying user about communication protocol in use. Internet explorer uses the concept of Zones. So we looked at this pattern in Tinba. No doubt for Internet Explorer, Tinba modifies the registry entry to disable configuration of Zones.as follows:
\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3
Tinba also manipulates the Firefox behavior by tampering user.js (preferences) file as follows
[C] user_pref("security.warn_submit_insecure",false);
Browser does not raise an alert box when information in sent over HTTP while submitting forms.
[C] user_pref("security.warn_viewing_mixed",false); :
Remove the warning of supporting mixed content over SSL.
The aim behind this modification is to remove the ambiguity in the communication channel used by Tinba. Let's have a look at the traffic communication:
 |
| Tinba Sending POST Requests |
 |
| Tinba Sending GET Requests |
 |
| Encrypted Reply |
 |
| Window Integrity Check on System Infected with Tinba on Every Reboot |
Some more next time !
Wednesday, June 13, 2012
LinkedIn Phishing Attack - Dissecting Attack and Used Exploit
Recently, after the successful intrusion of linked-in network by attackers, phishers also started exploiting the trust of users by sending phishing emails with embedded malicious links. The linked-in is on bit roll nowadays by attackers but it is always good to analyze the phishing attack. Our team received the phished linked-in emails. Of-course if you are in malware analysis field you are always targeted one or the other way. It happens. Let's discuss the exploit in action in this phishing attack. The users receive following email as presented in the figure below:
The users who received this email are presented below:
The malicious links accompanied with this email are presented as:
On successfully loading of JS files, the webpage redirects to the target pointed by document.location call. The target URL is actually NGINX reverse proxy which communicates back with blacklisted IP serving malware. The attacker is almost using 3-4 hops to retrieve the malicious content. On detecting the hosts, we found that some of the links are now down or giving forbidden access. However, the targets can be accessed by querying directly with the IP address of the host and not the DNS. The exploit used during this campaign might vary with time but we encountered the script that triggered flash/adobe exploit that uses JavaScript heap spraying. The obfuscated script used in this case is bit complex but not a hard target to deobfuscate. The obfuscated script (redacted) looks like as presented belowThe script is too big to paste here. So you can find it here - http://pastebin.com/MSpCtZH7
There are several tricks you can use to deobfuscate it, one of the methodology is discussed in our previous blog post on JavaScript Obfuscation - http://secniche.blogspot.com/2012/04/javascript-obfuscation-manual-armor-1.html.
The deobfuscated script is available here - http://pastebin.com/yDjQRD0u. Some of the interesting code has been shown below, the rest you can scratch on the pastebin.
 On successful, deobfuscation, we observed that
On successful, deobfuscation, we observed that1. The script is fingerprinting plugins, OS, User-agent and other information
2. The malicious domain is running BlackHole BEP.
3. We accessed certain set of files on the domain, one of which is shown below
So, the BlackHole is still on fire but attackers now using modular way of serving exploit. There are other interesting information that we found during analysis but not presenting here. If something more interesting comes up, we will update it here.
How to be secure?
1. Update plugins to the latest version.
2. Think twice before your click.
Be secure !
Tuesday, June 12, 2012
For Fun - XSS in ICE IX C&C Panel
Our team is working on ICE IX botnet analysis. We will be releasing a detailed paper about the working of ICE bot in coming time (very soon). However, this post is meant for some fun purposes but the provided information can be used to complete different tasks. We have detected an interesting XSS in main login page of ICE botnet C&C panel. It does not require any authentication as such though. The POC is presented in figure below
The interesting part is to understand the entry point in this as discussed.
Consider this, /adm/index.php?m=login , so usually "m" parameter in this URI is considered as an entry point which is true in certain sense. However, for this XSS, the entry point is present in /adm/index.php/ [Injection Point] ?m=login.
So, the point is, XSS finds its own entry points. :)
Browser Security Talk:
On additional note, the above presented screenshot shows that payload is sent in URL and Google Chrome parses it and then the payload becomes persistent. Seems like a bypass, yes it is. It depends whether Google Chrome team considers it or not. IE and NoScript triggers an alert.
Enjoy !
So what exactly you have to do is to hack the below XML construct in order to trigger it
.The interesting part is to understand the entry point in this as discussed.
Consider this, /adm/index.php?m=login , so usually "m" parameter in this URI is considered as an entry point which is true in certain sense. However, for this XSS, the entry point is present in /adm/index.php/ [Injection Point] ?m=login.
So, the point is, XSS finds its own entry points. :)
Browser Security Talk:
On additional note, the above presented screenshot shows that payload is sent in URL and Google Chrome parses it and then the payload becomes persistent. Seems like a bypass, yes it is. It depends whether Google Chrome team considers it or not. IE and NoScript triggers an alert.
Enjoy !
Subscribe to:
Posts (Atom)