UPDATE: http://www.secniche.org/papers/VB_2011_BRW_EXP_PACKS_AKS_RJE.pdf
An Official Malware Research Blog of SecNiche Security Labs. Analysis, straight from the hidden and underground.
Wednesday, March 14, 2012
Friday, March 9, 2012
CrossTalk - iPhone Malware Paradigm

We just released a new paper on iPhone Malware paradigm in CrossTalk Journal.
Abstract:The sphere of malware attacks is expanding to engulf the compact world of smartphones. This paper sheds light on exploitation tactics used by malware writers in designing iPhone applications that exploit the integrity of the victim’s phone. Our interest is in the harder problem of malware on iPhones that are not jailbroken.
Fetch the journal here: http://www.crosstalkonline.org/storage/issue-archives/2012/201203/201203-0-Issue.pdf
Monday, March 5, 2012
Intuit and BBB Under Targeted Attacks - Phishing (Malware)
About BBS and Intuit: Better Business Bureau is an ethical marketplace where buyers and sellers can trust each other, as defined here . Intuit provides a powerful software as a service platform.
ALERT: Be careful in clicking links.
BBB and Intuit are under targeted attacks. Other organization that is under targeted attacks. Phishing emails pointing to malicious domain serving obfuscated iframes are being thrown in the wild at a rapid pace. The emails look very legitimate but a single click can cause a serious damage. Since these are big organizations, we feel that risk is much higher. That's why the alert is here.
Malicious - Phishing Email Targeting - BBB

Malicious - Phishing Email Targeting - INTUIT

The gift that malicious domain send us is presented below(truncated version)

The deobfucation details of this script will be posted soon. We are analyzing other facets of this targeted attack.
ALERT: Be careful in clicking links.
BBB and Intuit are under targeted attacks. Other organization that is under targeted attacks. Phishing emails pointing to malicious domain serving obfuscated iframes are being thrown in the wild at a rapid pace. The emails look very legitimate but a single click can cause a serious damage. Since these are big organizations, we feel that risk is much higher. That's why the alert is here.
Malicious - Phishing Email Targeting - BBB

Malicious - Phishing Email Targeting - INTUIT

The gift that malicious domain send us is presented below(truncated version)

The deobfucation details of this script will be posted soon. We are analyzing other facets of this targeted attack.
Saturday, March 3, 2012
Cloud Infections on Fire - Amazon's WS
 It has been seen recently that Amazon's Web Service (AWS) has become the playground for attackers to host malware. Some incidents have been reported early. However, cloud services are providing a good storage as well as remote access property for serving malware through cloud. Attackers are always impressive in circumventing the normal operations of any cloud services in order to distribute malware effectively. We came across another incident in which malware is hosted at AWS server.
It has been seen recently that Amazon's Web Service (AWS) has become the playground for attackers to host malware. Some incidents have been reported early. However, cloud services are providing a good storage as well as remote access property for serving malware through cloud. Attackers are always impressive in circumventing the normal operations of any cloud services in order to distribute malware effectively. We came across another incident in which malware is hosted at AWS server.We started exploring the malware driven directory. The direct access to the directory was not allowed and we received following error.

This shows that the directory is in forbidden state which resulted in the HTTP error as presented above. We required to have direct link to the malicious executable. On analyzing further and gathering information, the Amazon cloud was hosting malware as shown below

After successful downloading, we analyzed that executable was packed with UPX packer with 33.6% compression. On unpacking, the code seemed to unroll a bit and presented us with some complex and lengthy code file. The executable file was actually a package file written in Borland. Its main functionality was to download another set of malicious files from different Amazon AWS directory. The complete set of files were downloaded into "c:\winsys" directory. We extracted another set of files as presented below

This shows that the package acts as a dropper. We take a look at one of the executable named as "BROWN.exe" which was packed with UPX again. So we unpacked it again to understand the crux.

The executable was written in "Visual Basic". So, we ran a check using anti virus and without a doubt it was a malware as shown below
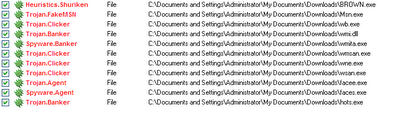
So we are not digging deeper. If you require samples, please drop us a line.
Subscribe to:
Posts (Atom)